Ethical Hacking Course in Hyderabad
with
100% Placement Assistance
- Expert Trainer with 12+ Years of Experience
- Life time access for live recording videos
- More focus on practical implementation
- Cover All modules SQL Injection, Cloud Computing
- 75 Days Advanced training programme
- Interview questions + interview guidance
OFFER: Pay Once and attend the running batch and an additional batch at Free of Cost.
Table of Contents
ToggleEthical Hacking Course in Hyderabad
Batch Details
| Trainer Name | Sanjay Kumar |
| Trainer Experience | 12+ Years |
| Next Batch Date | 20-November-2024 (07:00 PM IST) |
| Training Modes: | Online Instructor Led training |
| Course Duration: | 75 Days |
| Call us at: | +91 8186844555 |
| Email Us at: | brollyacademy@gmail.com |
| Demo Class Details: | ENROLL FOR FREE DEMO CLASS |
Ethical Hacking course In Hyderabad
Curriculum
Chapter 1.1: Information Security Overview
- What is Ethical Hacking?
- 5 Phases of Ethical Hacking
- Important Terminology
- Components of Information Security
- Functionality, Usability, and Security
Chapter 1.2: Information Security Attack and Threats vendors
- Objectives of Information Security Attacks
- Kinds of Information Security Threat and Attacks on the System
- Best Information Security Attack Vendors
- Information warfare
Chapter 1.3: Hacking
- Define Hacking, Hacker Classes and Hacker Phases
Chapter 1.4: Concepts of Ethical Hacking
- Importance of Ethical Hacking and its Extent and Restrictions
- Expertise of an Ethical Hacker
Chapter 1.5: Controls of Information Security
- Information Assurance
- Information Security Management Program
- Enterprise Information Security Architecture
- Network Security Zoning
- Policies of Information security
Chapter 1.6: Physical Security and Risk
- Kinds of Physical Security Control
- Important Roles and Functions in Risk Management
- Incident Management
- Identity and Access Management
Chapter 1.7: Information Security Laws and Standards
- Payment Card Industry Data Security Standard (PCI-DSS)
- Sarbanes Oxley Act (SOX)
- The Digital Millennium Copyright Act (DMCA)
- Federal Information Security Management Act (FISMA)
- Cyber Law in Different Countries
Chapter 2.1: Concepts of FootPrinting
- Types of Footprinting
- Footprinting Tools and Countermeasures
Chapter 2.2: FootPrinting through the Search Engines
Chapter 2.3: FootPrinting using Web Services
Chapter 2.4: Website FootPrinting and Email FootPrinting
Chapter 2.5: DNS FootPrinting and Network FootPrinting
- Fetching DNS Information and DNS examination tools
- Finding the Network Range
- Traceroute and Traceroute Tools
Chapter 2.6: Whis FootPrinting
Chapter 2.7: FootPrinting Tools
- Maltego and Recon-ng
- FOCA and Recon-Dog
- OSRFramework and Other FootPrinting Tools
Chapter 2.8: FootPrinting Counterattacks and Pen Testing
- FootPrinting Counterattacks
- FootPrinting Report Templates
- Network Scanning Technique
- Network Scanning Countermeasures
- Enumeration Techniques
- Enumeration Countermeasures
Chapter 5.1: Vulnerability Assessment Concepts
- Vulnerability Analysis and Categorization
- Kinds of Vulnerability Assessment
- Vulnerability Management Life cycle
Chapter 5.2: Vulnerability Assessment Solutions
Chapter 5.3: Vulnerability Scoring Systems
Chapter 5.4: Vulnerability Assessment Tools
- Nessus Professional
- GFI LanGuard
- Qualys Vulnerability Management
- Qualys FreeScan
- Nikto
- Retina CS
- OpenVAS
- SAINT
- Microsoft Baseline Security Analyzer
- Automated Vulnerability Detection System
- Vulnerability Assessment Tools for Mobile
Chapter 5.5: Vulnerability Assessment Reports
Vulnerability Assessment Reports Basics and Analyzing the Scanning Reports
- System Hacking methodology
- Steganography
- Steganalysis Attacks
- Covering Tracks
- Installation of VM’s in Windows and MAC
- Configuration of VM’s and Installing OS
- Installing Software
- Installation of VM’s in Windows and MAC
- Configuration of VM’s and Installing OS
- Installing Software
- Introduction to Metasploit
- Working with Metasploit
- Windows Hacking and Advanced Techniques
- Malware Fundamentals
- Types of Malwares
- Types of Trojans
- Trojan Analysis
- Trojan Countermeasures
- What is Sniffing
- Packet Sniffing Techniques
- MAC Attacks
- Sniffing Technique: DHCP Attacks
- Sniffing Technique: ARP Poisoning
- Spoofing Attacks
- CounterAttacks and Sniffing Detection Techniques
- What is Social Engineering Basics and Techniques
- Phishing Emails
- Types of Social Engineering Attacks
- Advanced Techniques
- Countermeasures
- Impersonation on Social Networking Sites
- Social Engineering Penetration Testing and Insider Threats
- What is Denial of Services (DoS)
- What is Distributed Denial of Services (DDoS)
- Types of Attacks
- DoS/DDoS Attack Techniques
- Botnets
- DDoS Attack Tools
- DoS and DDoS protection tools and Penetration Testing
- Session Hijacking Techniques
- Countermeasures
- Session Hijacking Tools and Counterattacks
- IPsec
- Firewall
- Intrusion Detection System (IDS)
- Honeypot Evasion Techniques
- IDS or Firewall Evading Tools
- Detecting Honeypots
- IDS and Firewall Evasion Counterattacks
- Firewall and IDS Penetration Testing
- Different Types of Webserver Attacks
- Attack Methodology
- Web Server Attack Tools
- Patch Management
- Counterattacks
- Web Server Security Tools
- Web Server Penetration Testing
- Different Types of Web Application Attacks
- Web Application
- Web App Threats
- Hacking Methodology
- Web App Security Testing Tools and Web App Pen TestingCountermeasures
- SQL Injection Concepts
- SQL Injection Attacks
- Types of SQL Injection and SQL Injection Methodology
- Injection Detection Tools
- Wireless Encryption
- Wireless Cracking Methodology
- Wireless Cracking Tools
- Bluetooth Hacking
- Wi-Fi Penetration Testing
- Counterattacks and Wireless Security Tools
- Mobile Platform Attack Vendors
- Hacking Android OS
- iOS Hacking
- Mobile Spyware and Mobile Device Management
- Mobile Security Guidelines and Tools
- Mobile Penetration Testing
- IoT Fundamentals
- IoT Attacks
- IoT Threats
- Hacking IoT Devices
- IoT Hacking Methodology and IoT Hacking Tools
- Counterattacks and IoT Penetration Testing
- Cloud Computing Techniques
- Various Cloud Computing Concepts
- Cloud Computing Threats
- Cloud Computing Attacks
- Security Techniques and Tools
- Different Types of Cryptography Ciphers
- Public Key Infrastructure (PKI)
- Cryptography Attacks
- Cryptanalysis Tools
- Fundamentals of Social Engineering
- Phishing Emails
- Types of Social Engineering Attacks
- Advanced Techniques
- Countermeasures
Ethical Hacking course in Hyderabad at Brolly Academy
Key Points
- Free Demo Class & Free Sessions: You get a free Ethical Hacking training demo class from our academy to get to know more about our faculty and the depth of the subject you will learn once you come on board.
- Train with our experts : Get trained with our industry experts in both online classes and offline methods to deliver high-quality education.
- Real Time Project Assisting : With our real-time projects, you get hands-on experience even before you enter the field of Ethical Hacking.
- Comprehensive Placement Support : We assist you 100% to get placed in the best company that Ethical Hacking has.
- Learning Materials : We have Specifically designed resources for Ethical Hacking have been prepared for our enrolled candidates alone, so that they can have the best learning material to come out as successful.
- Daily Course Recordings : We provide Recorded classes sent daily for the participants of online learning so that you can go through the lessons anytime.
- Guidance for the Ethical Hacker Certification Examination: We train you to take professional exams and enhance your credentials in certification by preparing you to perform well in the certification examination.
- Weekend Sessions for Doubt Clarification : We have weekend doubt sessions that helps you to clear all your doubts you have while reviewing the video classes provided.
- Interview Preparation : We prepare to be always ready for any interview in Ethical Hacking by conducting regular mock interviews.
- Hands on Training through Practice : With our hands-on training practice, you get to shine with the skill that you learned from us more when you go into the field of Ethical Hacking.
Overview of Ethical Hacking course in hyderabad in Brolly Academy
About
- Brolly Academy is proud to offer an inclusive Best Ethical Hacking Training in Hyderabad that is an intense blend of conceptual learning and practical exposure. We use a step-by-step approach to teaching so that the fundamentals are learned and hands-on skills are developed.
- We have an extended network in the city, our long experience in Ethical Hacking education has led to a chain of collaborations with various organizations as well as trainees.
- Our hacking course is specially designed to provide the basic knowledge, skills, and tools required for the job, with special training in Apache Spark.
- Practical real-time projects with real scenarios will be given to you so that you will have first-hand experience, all of which will lead to improvement and progress in your learning journey here in Hyderabad.
What is a Ethical Hacking?
Ethical Hacking or “white-hat hacking” is often defined as a deliberate exploration of computer systems, networks, or applications in order to pinpoint vulnerabilities and security weaknesses. In contrast to the malicious hacker, ethical hackers use their expertise to enhance security rather than take advantage of the situation.
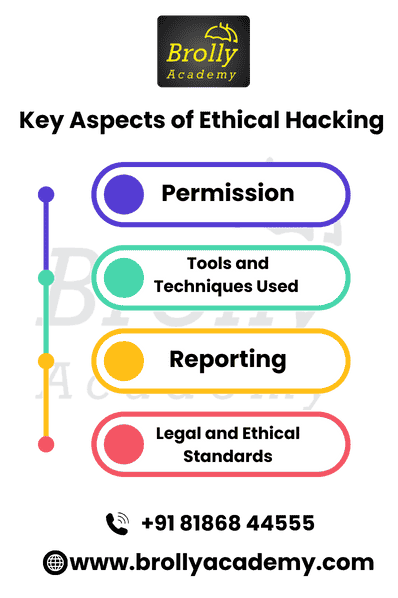
Key Aspects of Ethical Hacking:
- Permission : Ethical hackers always seek explicit permission from the organization before any test or assessment is performed. The primary goal is to seek out and remove security vulnerabilities so as not to let unauthorized people access and the data breach.
- Tools and Techniques Used : Penetration, Vulnerability scanning, and security auditing are some of the very commonly used tools and techniques by ethical hackers.
- Reporting : Ethical hackers submit detailed reports to the organizations once they test them, informing the organizations about the vulnerabilities found and make suggestions for improvement in security.
- Legal and Ethical Standards : Ethical Hacking operates within legal and ethical parameters to ensure that testing is conducted responsibly while being respectful of the privacy and integrity of the data. In general, Ethical Hacking is an integral part of strengthening cybersecurity by having organizations protect information systems from even potential risks.
Where is Ethical Hacking used?
- Corporate Security
- Companies apply Ethical Hacking by testing their systems, networks, and applications for vulnerabilities and ensuring that their data and customer information remain safe.
- Financial Institutions
- Banks and financial organizations perform Ethical Hacking as it pertains to cyberattacks, and they protect sensitive financial information.
- Government Agencies
- Here, governments use them to enhance national security and protect strategic structures from cyber attacks.
- Healthcare
- Many hospitals and healthcare institutions engage the services of ethical hackers in protecting patient records and keeping their standards according to HIPAA.
- E-commerce
- Online stores engage ethical hackers in their venture to keep customers' information and transactions secured for risk-free shopping.
- Telecommunications
- Network testing is, therefore done by various telecom firms to prevent unauthorized access to ensure the integrity of a communication system.
- Education
- Ethical Hacking is used by academic institutions to ensure the safety of students' and instructors' database, along with protecting the online learning platform.
- Software Development
- While developing the software, developers use Ethical Hacking to ensure that vulnerabilities should not surface once the product reaches the user's end.
- Cloud Computing
- Due to cloud migration, organizations face risk and vulnerabilities in terms of security. Ethical hackers test the strength of all security layers implemented to safeguard the sensitive data held online.
- IoT Devices
- Ethical Hacking identifies how a hacker could access connected devices in search of vulnerabilities in the IoT devices and ensure that the devices are safe.
- From a few perspective, Ethical Hacking is very indispensable across industries since there is vulnerability identification through putting in a wide security measure to counter cyber threats.
Ethical Hacking training in Hyderabad Brolly Academy
The Ethical Hacking course in Hyderabad at Brolly Academy provides a mix of theoretical knowledge and hands-on experience to build advanced cybersecurity skills.
Ethical Hacking syllabus Highlights
- In-Depth Introduction to Ethical Hacking
- Overview of information security principles and laws (PCI-DSS, SOX, DMCA, FISMA).
- Understanding the 5 Phases of Ethical Hacking.
- Footprinting & Reconnaissance
- Techniques for gathering information using tools like Maltego, Recon-ng, FOCA.
- Countermeasures against footprinting.
- Network Scanning & Enumeration
- Port scanning, identifying vulnerabilities, and extracting system information.
- Vulnerability Assessment
- Tools like Nessus, Qualys, OpenVAS for vulnerability detection and reporting.
- System Hacking & Exploitation
- Techniques for password cracking, privilege escalation, and steganography.
- Practical Labs with Virtual Machines & Kali Linux
- Setting up VMs and mastering Kali Linux for penetration testing.
- Advanced Tools & Techniques
- Utilizing Metasploit and understanding different malware types.
- Social Engineering & Insider Threats
- Techniques like phishing and impersonation, along with countermeasures.
- DoS & DDoS Attacks
- Mitigation strategies against DoS/DDoS attacks and botnets.
- Cryptography & Data Protection
- Fundamentals of cryptography, ciphers, and PKI.
- Industry-Standard Tools & Certifications
- Practice with tools like Wireshark, Burp Suite, and preparing for CEH certification in Hyderabad.
Modes
of Ethical Hacking course in Hyderabad
Online Training
- Flexible Learning
- Comprehensive Curriculum
- Practical Experience
- Expert Guidance
- Whatsapp support program.
- Lifetime access.
Video Course
- Self-Paced Learning
- Convenient Access.
- Clarification Sessions.
- Digital Certificate
- Whatsapp support program
- Lifetime access.
Corporate Training
- Hands-On Experience
- Personalized Coaching
- Interactive Learning
- Well-Equipped Classrooms
- Whatsapp support program
- Lifetime access.
Why Choose us
Ethical Hacking course online in Hyderabad at Brolly Academy

Experienced Trainers
Learn from our industry-leading instructors, who bring knowledge and experience to the classroom. Our Ethical Hacking trainers are dedicated to sharing their expertise in foundational and emerging technologies. Our trainers have 15+ years of experience training professionals and students, so they guarantee that you receive the best education possible.

Interactive Virtual Training
Informative online classes on Ethical Hacking. You can learn from your home and still enjoy working through rich interactive video content from current instructors. This allows us to train you in our video course program with live online sessions for your individual needs.

Extensive Job Placement Assistance
Our professionals with experience in career counselling guide you toward the development of the required job skills and your professional presence to ensure that the resume, interview, and job matching process, are commensurate to your specific skill set and your career goals. Further, our interviewing skills workshops ensure that you are prepared to win any job on the market.

Ethical Hacking Certification
Once you finish our Ethical Hacking course, you’ll receive a Brolly Academy certification, valued by employers. This Ethical Hacking certification in Hyderabad can strengthen your resume and support your career in cybersecurity.

Extensive Curriculum:
It would be an Ethical Hacking course that provides one with a comprehensive understanding of all the important concepts, techniques, and tools in cybersecurity-thus, taking you through from requirement gathering to stakeholder management.

Personalized Learning Experience:
Our trainers give Individual attention to the students is something we believe in. Our training batches are small in number, only 10 students, therefore, relatively personalized and, you would receive the best training following your distinct requirements. We provide online ethical hacking courses in Hyderabad
Market trend
1. Market Growth Rate
- Estimated CAGR: 14-16% from 2023 to 2030.
- Market Value: Valued at $4 billion (₹332 billion) in 2023, projected to reach $8-10 billion (₹664-830 billion) by 2030.
2. Cybersecurity Professional Requirement
- Job Growth: 28% growth for cybersecurity roles by 2030.
- Job Openings: 3.5 million jobs projected by 2025.
3. Industry Adoption
- Sector Investment: Finance, healthcare, and government sectors allocate 10-15% of IT budgets to security.
- Cloud Security Spending: Expected to exceed $50 billion (₹4.15 trillion) annually by 2025.
4. Certification Trends
- High demand for certifications like CEH, OSCP, with OSCP enrollments increasing by 20% in recent years.
5. Salary Impact
- Certified ethical hackers earn 20-30% more than non-certified peers.
- US-based certified experts average $100,000-$130,000 (₹8.3-10.8 million) annually.
6. Investment in Training
- Corporate Training: Companies spend $1,000-$2,500 (₹83,000-207,500) per employee on cybersecurity training.
- E-learning Growth: Cybersecurity courses, including Ethical Hacking, have a CAGR of 10-12%.
7. Emerging Technologies
- AI and Automation: 60% of companies expected to adopt AI-driven security tools by 2025.
Ethical Hacking training in Hyderabad
Testimonials
Certification
Ethical hacking certification course in Hyderabad
The Ethical Hacking course is conducted by a seasoned trainer who is renowned for his mastery of the subject. Brolly Academy issues a course completion certificate that may be accessed in paper and digital formats.
Brolly Academy’s Ethical Hacking course is perfect for Freshers and professionals looking to build or boost their cybersecurity careers. Known as the best institute for Ethical hacking in Hyderabad, it offers lifetime-valid certification to strengthen your resume
- Some of the most wide known Ethical Hacking certifications include
- Certified Ethical Hacker (CEH)
- The Offensive Security Certified Professional (OSCP)
- The Global Information Assurance Certification (GIAC)
- Certified Information Systems Security Professional
- Certified Hacking Forensic Investigator
- Certified Information Security Manager
Skills Developed
Best institute for Ethical hacking course in hyderabad
After taking our Best Ethical Hacking course in Hyderabad, you acquire a broad set of skills for a successful cybersecurity career.
- Information Security Overview
- You gain a comprehensive understanding of the fundamental principles of information security.
- Identification of Information Security Threats
- You learn to identify and rank several threats to information security.
- Knowledge of Attack Vectors
- Study various ways and trends followed by attackers against systems.
- Understanding Concepts of Ethical Hacking
- Learn ethical factors and methods defining Ethical Hacking.
- Understanding Security Laws and Standards
- Familiarize oneself with the legal and regulations-based framework governing Cyber Security.
- Techniques to Evade IDS, Firewalls, Honeypots
- Learn how to outsmart security to enter ethically.
- Hacking of Web Applications
- Understand how to identify vulnerabilities of web applications and how to defend them.
- Cloud Computing Security
- Keep abreast of the security issues of cloud services and how to keep safety in cloud-based systems.
- Cryptography
- Understand cryptographic techniques and their applications for the safeguarding of data.
With this comprehensive skill set, you’ll be well-equipped to really take on the tough cyber challenges in the real time and and set yourself up for success in the ever-evolving practice of Ethical Hacking.
Tools covered in Ethical Hacking course in hyderabad at Brolly Academy
This is an open source, powerful tool that allows network discovery and security auditing.
This is one of the most used network protocol analyzers that can help with the capture and analysis of packet data.
Metasploit Framework
It's such a flexible penetration testing tool to find and exploit vulnerabilities, made available to ethical hackers.
A well-known web application security testing platform which includes scanning and analysis. OWASP ZAP (Zed Attack Proxy) This is an open-source web application security scanner that helps to identify web application vulnerabilities.
Aircrack-ng
This suite of tools assists with the assessment of the security of Wi-Fi networks including packet capture and WEP/WPA/WPA2 key cracking. Password cracker, often used for password recovery it supports many encryption formats is known to be fast
This tool scans web server content and configuration for weaknesses.
It is an open-source, lightweight system that monitors network traffic in real-time for signs of unauthorized activity.
SQLMap
A manual tool, but it also discovers and exploits SQL injection vulnerabilities in a web application.
Social-Engineer Toolkit (SET)
This tool scans web server content and configuration for weaknesses.
Netcat
A networking utility to read and write data across network connections. Often used in network diagnostics.
Hashcat
A powerful password recovery tool; uses GPU acceleration to crack most types of hashes. Knowing these tools gets you up and running to identify security vulnerabilities in different environments.
Pre - requisites
Ethical Hacking Course in Hyderabad
Basic Knowledge of Computers
Understanding of computer operations, hardware, and software.
Networking Concepts
Knowledge about the basic concept of networking like IP addressing, subnetting, and protocols like TCP/IP, HTTP, FTP.
Operating Systems Knowledge
Knowledge of Windows and Linux operating systems. Most tools and techniques used by ethical hackers are Linux-based.
Knowledge of Security Fundamentals
Basic knowledge of security concepts and the kinds of threats and attacks
Analytical Thinking
Intelligent thinking applied to solving problems related to security
Prerequisite IT Experience (Optional)
While not required, having an experience in IT support, system administration, or even networking would be of benefit.
Readiness to learn
Continued learning in order to stay abreast with the latest cyber security trends and technology.
Job opportunities
CEH training in Hyderabad

Penetration Tester
He simulates cyber attacks to identify the vulnerability found within systems and applications Average Salary: ₹6-12 lakhs per year

Security Analyst
This person monitors security systems, analyzes events, and provides security solutions Average Salary: ₹4-10 lakhs per year

Information Security Consultant
He provides consultancy to an organization on security best practices and compliance
Average Salary: ₹8-15 lakhs per year

Cybersecurity Engineer
He designs and implements secure network solutions to mitigate cyber threats.
Average Salary: ₹6-14 lakhs per year.

Ethical Hacker
Concerned with a security assessment and penetration test to get an idea of the security posture of an organization.
Average Salary: ₹5-12 lakhs per year

Incident Responder
He or she is a person who investigates and resolves security breaches and cyberattacks. He develops a recovery strategy.
Average Salary: ₹6-12 lakhs per year

Forensic Analyst
He or she analyzes digital evidence in cybercrime investigations and security incidents. Average Salary: ₹5-10 lakhs per year

Vulnerability Assessment Analyst
It conducts systems and applications assessment in order to identify loopholes, and provides remedies for those. Average Salary: ₹4-9 lakhs per annum

Compliance Analyst
It ensures that different organizations are following the industry standards and security norms. Average Salary: ₹5-11 lakhs per year

Security Software Developer
Provides and develops security tools and software for data systems. Average Salary: ₹6-15 lakhs per annum Industry Demand and Growth
FAQ’s - About Brolly Academy
1. Which is the finest Ethical Hacking Training Institute in Hyderabad?
2. Ethical Hacking Training Fee in Hyderabad?
3. What is the average salary for an Ethical Hacking professional in Hyderabad?
4. What's Ethical Hacking training near my location?
Brolly Academy offers Ethical Hacking class training facilities at our centres in Ameerpet and KPHB, Hyderabad. Online classes are also available. You can enroll either through the website or by contacting us. +91 81868 44555
5. What if I miss a class?
6. Is placement assistance offered?
7. Who are the trainers at Ethical Hacking training in Hyderabad?
8. Who should take the course on Ethical Hacking?
9. What is the duration of the Ethical Hacking course in Hyderbad?
FAQ’s - General questions on Ethical Hacking
What is Ethical Hacking?
Types of Ethical Hacking
Various types like penetration testing, vulnerability assessment, web application testing, etc.
What skills does one need to be an ethical hacker?
What tools does an ethical hacker use?
Is Ethical Hacking illegal?
What does it mean to be the law when it is performed with authorization for the "right" purposes?
Which certifications are there for ethical hackers?
What is the job prognosis for ethical hackers?
Which are the sectors engaging the ethical hackers?
How much does an ethical hacker earn?
What is the difference between Ethical Hacking and Malicious Hacking?
What are the training courses for Ethical Hacking?
Different courses that exist online, through boot camps, and certification.











