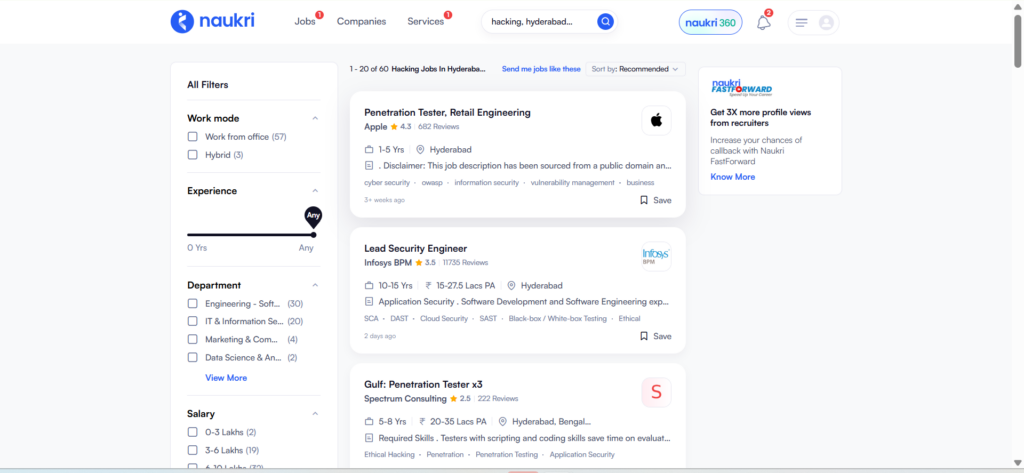
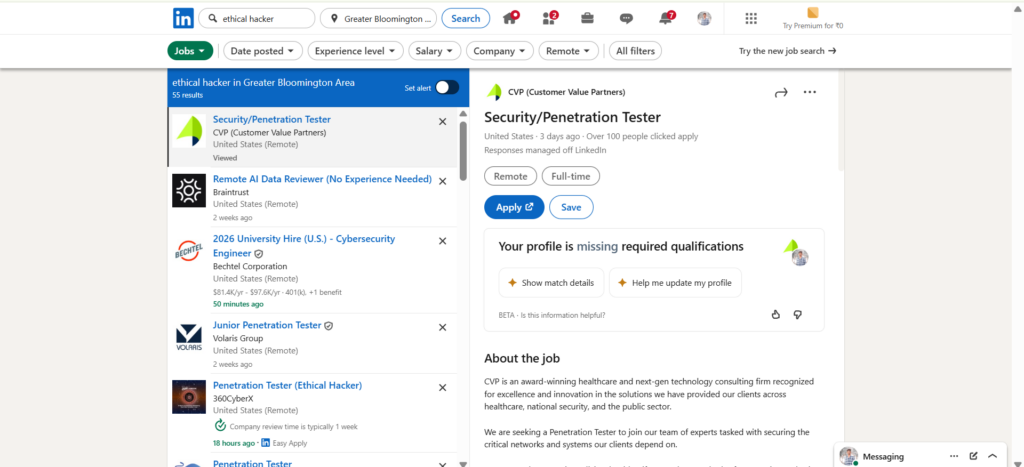
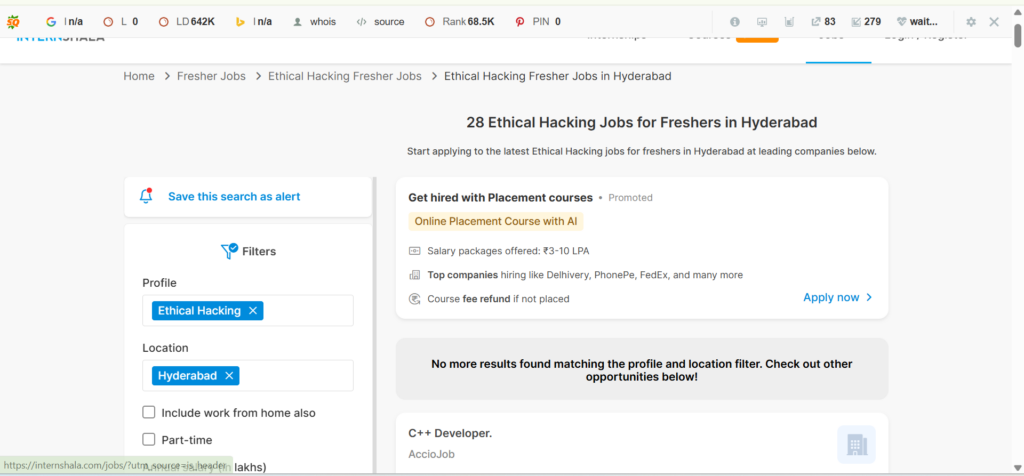
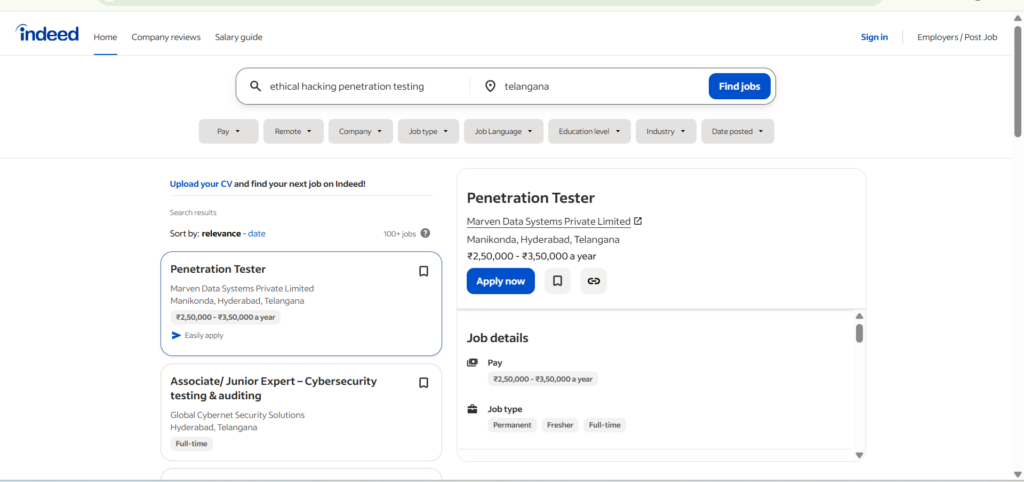
Perform practical labs on live systems, networks, and applications, with exposure to Windows Server Administration.
Ethical Hacking Course in Hyderabad
With
100% Placement & Job Guarantee Training*
Classroom Course | Online Course | Hands-on Labs | Real-Time Projects | 2–3 Months | Flexible Batches | Free Demo Class
At Brolly Academy, we offer industry-focused ethical hacking training in Hyderabad for beginners and professionals. Learn cyber security and ethical hacking through hands-on labs, real-world attack scenarios, and practical tools. The course covers CEH concepts, network & web security, vulnerability assessment, penetration testing, Kali Linux, and essential hacking tools. With expert trainers and flexible online & offline classes, we prepare you for roles like Ethical Hacker, Penetration Tester, and Cyber Security Analyst.
Table of Contents
ToggleEthical Hacking Course in Hyderabad
Next Batch Details
| Trainer Name | Mr. Sanjay Kumar |
| Trainer Experience | 15+ Real-Time Experience |
| Next Batch Date | 14 Jan 2026 |
| Training Modes: | Online Instructor-Led training |
| Course Duration: | 75 Days |
| Call us at: | +91 81868 44555 |
| Email Us at: | brollyacademy@gmail.com |
| Demo Class Details: | ENROLL FOR FREE DEMO CLASS |
Why Brolly Academy is the Best Ethical Hacking Training Institute in Hyderabad
12+ Years
Experience Expert-led ethical hacking training with real-world cybersecurity exposure.
300+
Google Reviews
4.8
Student Rating Highly rated for practical labs and clear teaching.
1000+
Students Trained Trusted by students, freshers, and professionals.
75 Days
Duration
Modes
Multiple Learning Modes Offline, online, and hybrid training options.
Fee Range
Affordable Fees Quality ethical hacking training with free demo access.
Practical Labs
Live attack simulations and real-time practice.
Why Choose Brolly Academy for Ethical Hacking in Hyderabad?
- Industry-ready ethical hacking curriculum
- Trainer with 12+ years cyber cybersecurity experience
- Hands-on labs with real attack simulations
- CEH-aligned ethical hacking concepts covered
- Kali Linux and penetration testing training
- Web and network security practical sessions
- Vulnerability assessment and exploitation labs
- Offline and online ethical hacking classes
- 75-day intensive ethical hacking program
- Beginner-friendly course with step-by-step flow
- Real-time tools used by ethical hackers
- Career-focused cyber security guidance
- Interview and job readiness support
- Affordable fees with a free demo class
- Flexible weekday and weekend batches
- Trusted by students and professionals in Hyderabad
Ethical Hacking classes in Hyderabad
Ethical Hacking Course Curriculum
Chapter 1.1: Information Security Overview
- What is Ethical Hacking?
- 5 Phases of Ethical Hacking
- Important Terminology
- Components of Information Security
- Functionality, Usability, and Security
Chapter 1.2: Information Security Attack and Threats vendors
- Objectives of Information Security Attacks
- Kinds of Information Security Threat and Attacks on the System
- Best Information Security Attack Vendors
- Information warfare
Chapter 1.3: Hacking
- Define Hacking, Hacker Classes and Hacker Phases
Chapter 1.4: Concepts of Ethical Hacking
- Importance of Ethical Hacking and its Extent and Restrictions
- Expertise of an Ethical Hacker
Chapter 1.5: Controls of Information Security
- Information Assurance
- Information Security Management Program
- Enterprise Information Security Architecture
- Network Security Zoning
- Policies of Information security
Chapter 1.6: Physical Security and Risk
- Kinds of Physical Security Control
- Important Roles and Functions in Risk Management
- Incident Management
- Identity and Access Management
Chapter 1.7: Information Security Laws and Standards
- Payment Card Industry Data Security Standard (PCI-DSS)
- Sarbanes Oxley Act (SOX)
- The Digital Millennium Copyright Act (DMCA)
- Federal Information Security Management Act (FISMA)
- Cyber Law in Different Countries
Chapter 2.1: Concepts of FootPrinting
- Types of Footprinting
- Footprinting Tools and Countermeasures
Chapter 2.2: FootPrinting through the Search Engines
Chapter 2.3: FootPrinting using Web Services
Chapter 2.4: Website FootPrinting and Email FootPrinting
Chapter 2.5: DNS FootPrinting and Network FootPrinting
- Fetching DNS Information and DNS examination tools
- Finding the Network Range
- Traceroute and Traceroute Tools
Chapter 2.6: Whis FootPrinting
Chapter 2.7: FootPrinting Tools
- Maltego and Recon-ng
- FOCA and Recon-Dog
- OSRFramework and Other FootPrinting Tools
Chapter 2.8: FootPrinting Counterattacks and Pen Testing
- FootPrinting Counterattacks
- FootPrinting Report Templates
- Network Scanning Technique
- Network Scanning Countermeasures
- Enumeration Techniques
- Enumeration Countermeasures
Chapter 5.1: Vulnerability Assessment Concepts
- Vulnerability Analysis and Categorization
- Kinds of Vulnerability Assessment
- Vulnerability Management Life cycle
Chapter 5.2: Vulnerability Assessment Solutions
Chapter 5.3: Vulnerability Scoring Systems
Chapter 5.4: Vulnerability Assessment Tools
- Nessus Professional
- GFI LanGuard
- Qualys Vulnerability Management
- Qualys FreeScan
- Nikto
- Retina CS
- OpenVAS
- SAINT
- Microsoft Baseline Security Analyzer
- Automated Vulnerability Detection System
- Vulnerability Assessment Tools for Mobile
Chapter 5.5: Vulnerability Assessment Reports
Vulnerability Assessment Reports Basics and Analyzing the Scanning Reports
- System Hacking methodology
- Steganography
- Steganalysis Attacks
- Covering Tracks
- Installation of VM’s in Windows and MAC
- Configuration of VM’s and Installing OS
- Installing Software
- Installation of VM’s in Windows and MAC
- Configuration of VM’s and Installing OS
- Installing Software
- Introduction to Metasploit
- Working with Metasploit
- Windows Hacking and Advanced Techniques
- Malware Fundamentals
- Types of Malwares
- Types of Trojans
- Trojan Analysis
- Trojan Countermeasures
- What is Sniffing
- Packet Sniffing Techniques
- MAC Attacks
- Sniffing Technique: DHCP Attacks
- Sniffing Technique: ARP Poisoning
- Spoofing Attacks
- CounterAttacks and Sniffing Detection Techniques
- What is Social Engineering Basics and Techniques
- Phishing Emails
- Types of Social Engineering Attacks
- Advanced Techniques
- Countermeasures
- Impersonation on Social Networking Sites
- Social Engineering Penetration Testing and Insider Threats
- What is Denial of Services (DoS)
- What is Distributed Denial of Services (DDoS)
- Types of Attacks
- DoS/DDoS Attack Techniques
- Botnets
- DDoS Attack Tools
- DoS and DDoS protection tools and Penetration Testing
- Session Hijacking Techniques
- Countermeasures
- Session Hijacking Tools and Counterattacks
- IPsec
- Firewall
- Intrusion Detection System (IDS)
- Honeypot Evasion Techniques
- IDS or Firewall Evading Tools
- Detecting Honeypots
- IDS and Firewall Evasion Counterattacks
- Firewall and IDS Penetration Testing
- Different Types of Webserver Attacks
- Attack Methodology
- Web Server Attack Tools
- Patch Management
- Counterattacks
- Web Server Security Tools
- Web Server Penetration Testing
- Different Types of Web Application Attacks
- Web Application
- Web App Threats
- Hacking Methodology
- Web App Security Testing Tools and Web App Pen TestingCountermeasures
- SQL Injection Concepts
- SQL Injection Attacks
- Types of SQL Injection and SQL Injection Methodology
- Injection Detection Tools
- Wireless Encryption
- Wireless Cracking Methodology
- Wireless Cracking Tools
- Bluetooth Hacking
- Wi-Fi Penetration Testing
- Counterattacks and Wireless Security Tools
- Mobile Platform Attack Vendors
- Hacking Android OS
- iOS Hacking
- Mobile Spyware and Mobile Device Management
- Mobile Security Guidelines and Tools
- Mobile Penetration Testing
- IoT Fundamentals
- IoT Attacks
- IoT Threats
- Hacking IoT Devices
- IoT Hacking Methodology and IoT Hacking Tools
- Counterattacks and IoT Penetration Testing
- Cloud Computing Techniques
- Various Cloud Computing Concepts
- Cloud Computing Threats
- Cloud Computing Attacks
- Security Techniques and Tools
- Different Types of Cryptography Ciphers
- Public Key Infrastructure (PKI)
- Cryptography Attacks
- Cryptanalysis Tools
- Fundamentals of Social Engineering
- Phishing Emails
- Types of Social Engineering Attacks
- Advanced Techniques
- Countermeasures
Ethical Hacking Training In Hyderabad
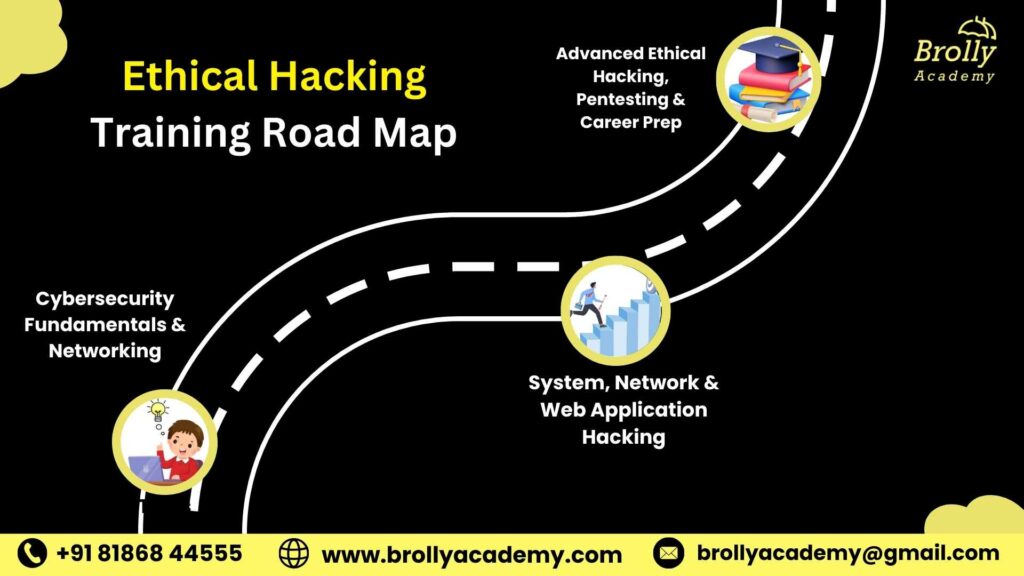
Ethical Hacking Training Roadmap – Beginner to Advanced
Our Ethical Hacking Course in Hyderabad is structured into clear learning phases across 75 days. Each phase focuses on building practical cyber security skills with hands-on labs, real-world attack simulations, and industry-relevant tools—so learners gain job-ready ethical hacking expertise, not just theory.
01
Phase 1: Cybersecurity Fundamentals & Networking
- Introduction to Ethical Hacking & Cyber Laws
- Types of Hackers, Threats & Attacks
- Networking Fundamentals (TCP/IP, Ports, Protocols)
- Linux Basics & Windows Security
- Virtual Labs Setup (Kali Linux, VirtualBox)
- Information Gathering & Footprinting
- Hands-on practice with real-time scenarios
02
Phase 2: System, Network & Web Application Hacking
- Scanning & Enumeration Techniques
- Vulnerability Assessment & Exploitation
- Password Cracking & Social Engineering
- Web Application Hacking (SQL Injection, XSS, CSRF)
- Wireless Network Hacking (Wi-Fi Attacks)
- Malware Basics & Sniffing Techniques
- Tools: Nmap, Metasploit, Burp Suite, Wireshark
03
Phase 3: Advanced Ethical Hacking, Pentesting & Career Prep
- Advanced Exploitation & Privilege Escalation
- Web Server & Cloud Security Basics
- Penetration Testing Methodology
- Bug Bounty & Real-Time Case Studies
- Documentation & Security Reporting
- CEH Certification Guidance
- Resume Building, Mock Interviews & Placement Support
What is Ethical Hacking?
- Ethical Hacking Explained – Ethical hacking is the legal practice of finding security weaknesses in systems to protect them from cyber attacks.
- Legal & Authorised Hacking – Ethical hackers work with permission to test networks, websites, and applications safely.
- Finds Security Vulnerabilities – It helps identify loopholes in systems before real hackers can exploit them.
- Protects Networks & Data – Ethical hacking improves network security and safeguards sensitive data.
- Uses Real Hacking Tools – Ethical hackers use tools like Kali Linux, Nmap, and Metasploit for testing.
- Includes Penetration Testing – Simulates real-world cyber attacks to check system strength.
- Part of Cyber Security – Ethical hacking is a core skill within cyber security and information security.
- High Career Demand – Ethical hacking skills are in demand for roles like Ethical Hacker and Cyber Security Analyst.
Where Ethical Hacking Is Used
Industry | How It’s Used | Example |
IT & Software Companies | Secures applications and networks | Penetration testing for company websites |
Banking & Financial Services | Secures financial systems and ensures safe transactions | Testing online banking security |
E-Commerce & Retail | Prevents data breaches and fraud | Securing payment gateways |
Healthcare | Safeguards patient data and systems | HIPAA-compliant security testing |
Telecom & Internet Providers | Secures large-scale networks | Network vulnerability assessments |
Government & Defense | Protects critical infrastructure | National cyber security audits |
Cloud & Data Centres | Ensures cloud environment security | AWS and Azure penetration testing |
Startups & Tech Firms | Develops products with security built in from the start | Security testing before product launch |
Education Institutions | Protects student data and systems | Campus network security testing |
Mobile & App Development | Protects mobile apps from security threats | Android and iOS app security testing |

Benefits of the Ethical Hacking Course in Hyderabad
Benefits of the Course
At Brolly Academy, we offer Ethical Hacking training in Hyderabad with both online and offline classroom modes, led by industry experts with real-world cybersecurity experience.
1. Learn from Expert Ethical Hackers
Step-by-step training guided by certified cybersecurity professionals.
2. Master Cyber Security Tools
Hands-on practice with Kali Linux, Metasploit, Nmap, Burp Suite, and more.
3. Work on Real-Time Attacks
4. Strong Networking Fundamentals
Understand TCP/IP, ports, protocols, firewalls, and network security.
5. Web Application Security Skills
Learn to find and fix vulnerabilities like SQL Injection and XSS, aligned with SOC Analyst practices.
6. System & Server Hacking
Gain skills in Windows and Linux system exploitation techniques.
7. Learn Malware & Threat Analysis
Understand malware behaviour, trojans, and ransomware basics.
8. Penetration Testing Expertise
Perform vulnerability scanning and penetration testing professionally.
9. Wireless & Mobile Security
Secure Wi-Fi networks and test Android application vulnerabilities.
10. Hands-on Labs & Practice
Real lab environments for continuous practical exposure.
11. Industry-Relevant Skills
Skills applicable in IT companies, enterprises, and security teams.
12. Certification Preparation
Prepare for global certifications like CEH and Security+.
13. Job & Career Support
Resume preparation, interview training, and placement guidance.
14. Affordable Course Fees
High-quality Ethical Hacking training at competitive pricing.
15. Flexible Learning Options
Choose online or offline classes with convenient schedules.
Thinking of an Ethical Hacking Course in Hyderabad?
- Traditional Training
- You mostly listen to theory with limited hands-on practice
- Focus on notes, slides, and outdated hacking concepts
- Trainers with only basic cybersecurity knowledge
- Occasional labs, not real attack simulations
- Limited exposure to real-world cyber threats
- Support ends after course completion
- Small exercises with no real-time impact
- Minimal job or placement assistance
- One-size-fits-all training approach
- Brolly Academy Training
- Learn ethical hacking and cybersecurity from day one
- Covers the latest cyber attacks, tools, and defence techniques
- Multiple live digital marketing projects for real experience.
- Daily hands-on labs with real attack scenarios
- Work on live systems and real-world vulnerabilities
- Continuous guidance until job placement
- Real-time penetration testing projects
- Resume building, interview prep, and placement support
- Personalised mentoring based on career goals
Best Ethical Hacking training Institute in Hyderabad
Meet Your Ethical Hacking Trainer
INSTRUCTOR
Mr. Sanjay Kumar
Ethical Hacking & Cyber Security Expert
15+ Years Experience
About the tutor:
- Sanjay Kumar has over 15 years of hands-on experience in ethical hacking, cybersecurity, and network security, working with real-world attack and defence scenarios.
- He specialises in penetration testing, vulnerability assessment, network security, web application security, and cyber threat analysis.
- With 15+ years as a trainer, Mr. Sanjay’s teaching style makes complex hacking concepts easy to understand for both beginners and advanced learners.
- His practical, lab-driven approach helps students gain real-time ethical hacking skills required for SOC Analyst and Ethical Hacker roles.
- He focuses on job-oriented training, ensuring students are industry-ready with strong technical and problem-solving skills.
Known for his supportive and professional mentoring style, Mr. Sanjay Kumar is recognised as a trusted ethical hacking trainer in Hyderabad.

Ethical Hacking Training Institute in Hyderabad
Skills Developed after the course
- Understand the fundamentals of ethical hacking and cybersecurity
- Perform vulnerability assessment and penetration testing (VAPT)
- Use industry tools like Kali Linux, Nmap, Metasploit, and Burp Suite
- Identify and exploit network security vulnerabilities
- Secure systems against malware, ransomware, and cyber attacks
- Test and protect web applications using OWASP Top 10
- Analyse Wi-Fi and wireless network security
- Perform Linux and Windows system hacking
- Learn cyber forensics and incident response basics
- Monitor threats using SOC and security monitoring concepts
- Understand ethical hacking methodologies and frameworks
- Gain job-ready skills for Ethical Hacker and SOC Analyst roles
Ethical Hacking Course Institute in Hyderabad
Ethical Hacking Capstone Projects Covered
1. Network Penetration Testing Project
Work on live networks to identify vulnerabilities, scan open ports, analyse firewalls, and exploit network weaknesses using ethical hacking tools.
2. Web Application Security Testing Project
Test real web applications for SQL Injection, XSS, CSRF, authentication flaws, and OWASP Top 10 vulnerabilities.
3. System Hacking & Privilege Escalation Project
Perform Windows and Linux system exploitation, password cracking, privilege escalation, and access control bypass techniques.
4. Wireless & Wi-Fi Security Testing Project
Analyse wireless networks, crack WPA/WPA2 encryption, detect rogue access points, and secure Wi-Fi infrastructures.
5. Vulnerability Assessment & Reporting Project
Conduct full vulnerability scans using industry tools, analyse risks, and prepare professional VAPT reports.
6. Malware Analysis & Cyber Threat Project
Study malware behaviour, trojans, ransomware basics, and understand real-world cyber attack patterns and defence methods.
Ethical Hacking Course Fee & Offerings in Hyderabad
Ethical Hacking Training Fee & Offerings
Video Recording
Rs 15000 9999
- Lifetime access to recorded sessions
- Ethical hacking basics to advanced concepts
- Kali Linux & hacking tools covered
- 80+ recorded classes
- Real-time lab demonstrations
- Resume preparation support
- Interview guidance included
- WhatsApp group access
Class Room Training
Rs 35000 29999
- 75 days of structured classroom training
- Training by expert ethical hackers
- Daily hands-on practical labs
- Real-time penetration testing projects
- One-on-one mentoring & lab support
- Weekly mock interviews
- Resume building & interview prep
- Soft skills & aptitude training
- Dedicated placement support
- WhatsApp support + community access
Online Course
Rs 30000 24999
- Live interactive online classes
- 75-day complete training program
- Daily recorded sessions for revision
- Real-time hacking labs & projects
- Weekend & weekday batch options
- Doubt-clearing sessions
- Resume templates & guidance
- WhatsApp group access
Placement Program for Ethical Hacking Training in Hyderabad
Placement Program
At Brolly Academy, our Ethical Hacking Course in Hyderabad includes 100% placement support, ensuring students gain real-world cyber security skills and secure jobs in top companies.

Resume Building

Placement Training

Interview Questions

Realtime Live Projects

Get Offer Letter

Scheduling Interviews

Mock Interviews

Personality Development
- Resume Building – ATS-friendly resumes tailored for Ethical Hacker and SOC Analyst roles.
- Placement Training – Learn how to apply for cybersecurity jobs and crack hiring processes.
- Interview Questions – Practice technical and HR ethical hacking interview questions.
- Internships under Experts – Hands-on exposure to real-world cybersecurity projects.
- Real-Time Live Projects – Work on penetration testing and vulnerability assessment projects.
- Aptitude Preparation – Improve logical reasoning and problem-solving skills.
- Personality Development – Build communication skills and professional confidence.
- Mock Interviews – Simulated interviews to boost real interview confidence.
- Scheduling Interviews – We connect you with hiring partners and schedule interviews.
- Get Offer Letter – Secure ethical hacking job offers in Hyderabad and across India.
What Our Students Say About Ethical Hacking Training in Hyderabad
Testimonials
Leon
@Leon
I joined the Brolly Academy for the Ethical Hacking course in hyderabad and it was the best experience. I enjoyed the course very much and I learned a lot from it. The instructors were very knowledgeable and very experienced in the Ethical Hacking field. I would highly recommend this course for anyone who wants to get started with Ethical Hacking.
Ramesh
@Ramesh
The Ethical Hacking course in hyderabad offered by Brolly Academy is so good as they have a great training staff and the course is very well organized. The instructors are very experienced, knowledgeable and friendly. They provide individual attention to each student and help them with their queries which is a great thing.
Nitin
@Nitin
I enrolled for the Ethical Hacking video course at Brolly Academy and found it so helpful and easy. The classroom recordings were so clear and the instructors were very well versed with the subject. They explained each and every concept so well that it was easy to understand even the toughest of topics. The course content is also very detailed and covers everything related to Ethical Hacking.
Tanzeel
@Tanzeel
Ethical Hacking online course training in hyderabad at Brolly Academy is the best. The classes were taken regularly at convenient timings and the instructors were very patient and helpful. I did not feel like I was learning something new, but it felt more like an update on my existing knowledge base. I would recommend Brolly Academy for anyone looking to take up Ethical Hacking online course training in hyderabad.
Preethika
@Preethika
Brolly Academy's Ethical Hacking placement assistance in Hyderabad is so useful. They train and prepare you with mock interviews and also help with the interview process. They also gave me additional tips that helped me alot during my interviews. I would recommend Brolly Academy's Ethical Hacking placement training to anyone who is looking for a career in the IT industry.
Ethical Hacking Student Community in Hyderabad
Student Community

Learning & Collaboration
Work together with fellow students on ethical hacking labs, penetration testing tasks, and cybersecurity challenges as a team.

Access to Resources and Tools
Get exclusive access to ethical hacking tools, lab environments, recorded sessions, and updated cybersecurity resources.

Networking Opportunities
Build your professional network by connecting with cybersecurity professionals, ethical hackers, SOC analysts, and recruiters in Hyderabad.

Mentorship from Industries Professional
Learn directly from experienced ethical hackers and cybersecurity experts through mentoring and real-world insights

Job Support and Career Development
Stay updated with cybersecurity job openings, internships, live projects, and placement assistance.
Ethical Hacking Training in Hyderabad
Pre-requisites & Eligibility
Our Ethical Hacking Course in Hyderabad is designed for learners from all backgrounds. Whether you are starting your cybersecurity career or upgrading your IT skills, this program is structured to help you succeed. No prior hacking experience is required—just curiosity and a passion for cyber security.
- No Technical Skills Required- Beginners with basic computer knowledge can start ethical hacking from scratch.
- Students & Graduates- Ideal for students and fresh graduates looking to build a career in cybersecurity.
- Freshers & Career Starters- Perfect for freshers aiming for Ethical Hacker or SOC Analyst roles.
- Working Professionals- IT and non-IT professionals can upskill into cybersecurity and ethical hacking.
- Entrepreneurs & Business Owners- Learn to secure business systems, networks, and customer data.
- Freelancers- Build skills for penetration testing, security audits, and cyber consulting.
- Job Seekers- Placement-focused training for candidates seeking cybersecurity jobs.
- Global Career Aspirants- Ethical hacking skills are in demand worldwide, opening global opportunities.

Who Should Learn Ethical Hacking Training in Hyderabad?

- Students- Begin your journey in cybersecurity and build strong ethical hacking fundamentals with hands-on labs.
- Fresh Graduates- Start a high-demand career in ethical hacking, penetration testing, and SOC roles.
- Job Seekers & Career Switchers- Transition into cybersecurity from IT or non-IT backgrounds with job-oriented training.
- Working Professionals- Upgrade your skills in cybersecurity, network security, and ethical hacking tools.
- Entrepreneurs & Business Owners- Learn how to protect business data, systems, and customer information from cyber threats.
- Freelancers- Offer ethical hacking services such as penetration testing and vulnerability assessment.
- Home Makers- Enter the cybersecurity field with structured training and flexible learning options.
Ethical Hacking Career Opportunities in Hyderabad
Career Opportunities

- Ethical Hacker- Identifies and fixes security vulnerabilities in systems, networks, and applications.
- Penetration Tester- Performs authorised attacks to test security strength and prevent real cyber threats.
- Cyber Security Analyst- Monitors systems, detects threats, and responds to security incidents.
- SOC Analyst- Works in Security Operations Centres to analyse logs, alerts, and attacks.
- Network Security Engineer- Designs and secures enterprise networks against cyber attacks.
- Information Security Analyst- Ensures compliance, risk management, and data protection policies.
- Vulnerability Assessment Specialist- Identifies security flaws and prepares professional VAPT reports.
- Incident Response Engineer- Handles real-time cyber incidents and system breach investigations.
- Malware Analyst- Analyses malware behaviour and develops threat mitigation strategies.
- Cyber Security Consultant- Advises organisations on security architecture and protection strategies.
Over 20,000+ job openings available for Ethical Hacking in Hyderabad for freshers
Ethical Hacking Salary in Hyderabad – 2026
Ethical Hacking Role | Average Salary (Freshers) | Average Salary (Mid-Level) | Average Salary (Experienced) |
Ethical Hacker / Cyber Security Analyst | ₹3 – 5 LPA | ₹6 – 10 LPA | ₹12 – 18+ LPA |
Penetration Tester | ₹4 – 6 LPA | ₹8 – 12 LPA | ₹15 – 20+ LPA |
SOC Analyst | ₹3.5 – 5.5 LPA | ₹7 – 11 LPA | ₹14 – 18 LPA |
Network Security Engineer | ₹4 – 6.5 LPA | ₹8 – 13 LPA | ₹15 – 22 LPA |
Cyber Security Consultant | ₹5 – 7 LPA | ₹10 – 15 LPA | ₹18 – 30+ LPA |
Best Ethical Hacking Training Institute in Hyderabad with Placements
Our Achievements
Completed 120+ Batches
15+ Years of Training Experience
1200+ Students Trained
Trusted Cyber Security Training Provider
Ethical Hacking Certification Training Institute in Hyderabad
Ethical Hacking Certifications You Will Receive
After completing the Ethical Hacking Course in Hyderabad at Brolly Academy, you will receive industry-recognised certifications that validate your cybersecurity skills and practical experience. These certifications strengthen your resume and improve your chances of securing ethical hacking and cybersecurity roles.
- Ethical Hacking Course Completion Certificate
- Ethical Hacking Internship Certification
- Cyber Security & Network Security Certification
- Vulnerability Assessment & Penetration Testing (VAPT) Certification
- SOC Analyst Fundamentals Certification
- Live Project Experience Certificate
Market Trends of Ethical Hacking Course
Market Trends
- Rise in Cyber Attacks – Increasing data breaches and cyber threats are driving demand for ethical hackers across industries.
- Growing Demand for Cyber Security Professionals – Organisations are actively hiring ethical hackers, SOC analysts, and penetration testers.
- Cloud & Network Security Focus – With cloud adoption, securing cloud infrastructure and enterprise networks is a top priority.
- AI in Cyber Security – AI-powered threat detection and automated security tools are transforming ethical hacking practices.
- VAPT as a Core Requirement – Vulnerability Assessment and Penetration Testing is now mandatory for many organisations.
- Remote & Global Job Opportunities – Ethical hacking skills open doors to global and remote cybersecurity roles.
- Compliance & Data Protection Laws – Regulations like GDPR and ISO standards increase the need for security audits.
- Market Growth – The cybersecurity industry is growing rapidly, creating long-term career opportunities worldwide.

Ethical Hacking Training in Hyderabad
FAQS
1. What is ethical hacking in simple words?
Ethical hacking means finding security weaknesses in systems legally to protect them from real hackers. Ethical hackers help organisations stay safe.
2. Is ethical hacking legal in India?
Yes. Ethical hacking is 100% legal in India when done with proper authorisation and ethical intent, as taught at Brolly Academy.
3. Who can learn ethical hacking?
Anyone with basic computer knowledge can learn ethical hacking, including students, freshers, working professionals, freelancers, and career switchers.
4. What is the eligibility for an ethical hacking course?
There are no strict eligibility criteria. Basic computer awareness and interest in cybersecurity are enough to start.
5. Is coding required for ethical hacking?
No. Coding is not mandatory for beginners. At Brolly Academy, coding is taught gradually only where required.
6. Which is the best ethical hacking course in Hyderabad?
Brolly Academy’s Ethical Hacking Course in Hyderabad is designed with hands-on labs, real-time projects, and placement support.
7. How much does an ethical hacking course cost in Hyderabad?
At Brolly Academy, the ethical hacking course fee is affordable and value-based, with online and offline options.
8. What is the duration of an ethical hacking course?
The Ethical Hacking Course at Brolly Academy has a 75-day structured training program.
9. Is CEH certification worth it?
Yes. CEH is a globally recognised certification, and our course prepares students with CEH-aligned concepts and skills.
10. What are the tools used in ethical hacking?
Students learn tools like Kali Linux, Nmap, Metasploit, Wireshark, Burp Suite, Nessus, SQLmap, and more.
11. Can beginners learn ethical hacking?
Yes. Our course is beginner-friendly, starting from the basics and moving to advanced ethical hacking concepts step by step.
12. What jobs can I get after ethical hacking?
You can apply for roles such as Ethical Hacker, Penetration Tester, SOC Analyst, Cyber Security Analyst, and Security Consultant.
13. What is the salary of an ethical hacker in Hyderabad?
Salaries vary by skill and role, but ethical hacking offers strong growth potential in Hyderabad’s IT and cybersecurity market.
14. Is ethical hacking a good career in 2025?
Yes. With rising cyber threats, ethical hacking remains a high-demand and future-proof career in 2025 and beyond.
15. What is the difference between hacking and ethical hacking?
Hacking is illegal, while ethical hacking is legal, authorised, and focused on security protection.
16. Does ethical hacking require mathematics?
Only basic logical thinking is needed. Advanced mathematics is not required for most ethical hacking roles.
17. Is ethical hacking difficult to learn?
No. With the right training and hands-on practice, ethical hacking is easy to understand and learn.
18. Can I learn ethical hacking without a degree?
Definitely. Many entrepreneurs join our course to learn how to generate leads, run ads, and grow their businesses online.
19. What are the prerequisites for CEH training?
Basic knowledge of computers and networking is helpful, which is covered from scratch at Brolly Academy.
20. Is ethical hacking part of cybersecurity?
Yes. Ethical hacking is a core part of cybersecurity, focusing on identifying and fixing vulnerabilities.
21. Are there offline ethical hacking classes in Hyderabad?
Yes. Brolly Academy offers offline classroom ethical hacking training in Hyderabad, along with online options.
22. Does the ethical hacking course include placement support?
Yes. Our course includes resume building, mock interviews, internships, and placement assistance.
23. What is penetration testing in ethical hacking?
Penetration testing means legally testing systems by simulating attacks to identify security gaps.
24. Will I get guidance on building a career in digital marketing?
Kali Linux is used for penetration testing, vulnerability assessment, and ethical hacking labs.
25. Can ethical hackers work as freelancers?
Yes. Many ethical hackers work as freelancers offering security audits and penetration testing services.
26. How long does it take to become an ethical hacker?
With focused training, you can start ethical hacking within 3 to 6 months, depending on practice.
27. Is ethical hacking safe as a career?
Yes. Ethical hacking is a legal, respected, and secure career path with long-term demand.
28. Which certification is best for ethical hacking?
CEH is popular, but skills, hands-on projects, and real-time exposure are equally important.
29. What is the scope of ethical hacking in India?
India has a huge demand for ethical hackers across IT companies, startups, banks, and enterprises.
30. How do I choose the right ethical hacking institute in Hyderabad?
Choose an institute like Brolly Academy that offers hands-on labs, experienced trainers, real-time projects, and placement support.
Other Relevant Courses
Got more questions?
Talk to Our Team Directly
Contact us and our academic councellor will get in touch with you shortly.